Moving applications and data into public clouds is an easy way for enterprises to simplify cooperation among geographically dispersed teams and use compute and storage resources in a more efficient way. But those advantages come at a price. Transporting data from secured premises into the private cloud is risky, as is, sharing compute and storage resources with other stakeholders. The business advantages are difficult to weigh up against the risk, leading to time-consuming evaluations, and delaying a business step with huge potential Providers of public cloud services need to assure security and integrity of customer data if they want to get enterprises to move their data from enterprise sites and private clouds into public clouds.
Securing the cloud
Data center operators have made significant investments in protecting the cloud. They are using virtualization technologies to securely separate shared resources in order to minimize the risk posed by malicious neighbors. Sophisticated firewalls and intrusion detection systems analyze traffic and identify malicious activities. Intelligent algorithms can learn from previous attacks and even identify new attack vectors that are using similar penetration patterns. While the ability to identify and prevent attacks continuously increases, there is an ongoing arms race between malicious actors and corporate security teams.
Learning from the past
When it comes to protecting networks and data, one of the key challenges is ever-increasing complexity. Complexity is also a key barrier against creating trust. There is a need for basic, simple concepts that create a high level of confidence with transparency and inherent credibility.
Prior to our age of hyper-connectivity, an “airgap” between systems, keeping them strictly isolated from each other, was seen as the ultimate way to secure networks. Service providers operated parallel networks with equipment dedicated to specific customers or customer segments. But this approach has become less attractive as unintended connectivity, such as multi-cloud access instantiated over public or untrusted networks, easily circumvents the carefully designed airgap.
It may, however, be time to reconsider the airgap approach. Most security controls aim at protecting networks at the transport and application layer. Those tools are able to reliably identify network intrusion and malicious activity. Hence, attackers focus on compromising lower-layer operating systems, exploiting vulnerabilities of boot processes or hardware weaknesses in servers and processors such as Spectre and Meltdown. Security controls at higher network layers cannot mitigate these attack vectors.
Best practice cloud security
Creating an airgap between systems serving multiple customers and/or applications comes into play again. A pragmatic separation of hardware eliminates the risk of attacks spreading across different customers and applications hosted in the cloud. The security advantage of such an approach is easy to explain, especially when applied in combination with securing the network connection with encryption to mitigate risk from untrusted networks.
The following measures for cloud-based security should be taken:
- Securing the network connectivity with end-point encryption. The encryptor should be tightly integrated, directly applied at the network interface to secure all traffic and also protect against vulnerabilities of the software stack.
- For high-security requirements, network protection should include isolating physical server and storage resources.This brings the principle of physical perimeter security to the public cloud, extended the enterprise perimeter in a secure way over encrypted links into a physically separated and protected cloud zone. Instead of offering virtual private servers, moving to dedicated bare-metal with secure operating systems ensures confidence in the security of hosting services.
Applying security controls for the cloud – a use case
ADVA is a technology partner for secure cloud connectivity solutions, offering software NFV hosting and orchestration products as well as demarcation devices to securely connect enterprises with the cloud. These demarcation solutions with integrated edge compute nodes can connect the cloud over any underlay technology. VNFs provide SD-WAN and network security functions, while the network operating system comes with a rich set of in-built security capabilities that protect the network at the lowest layer.
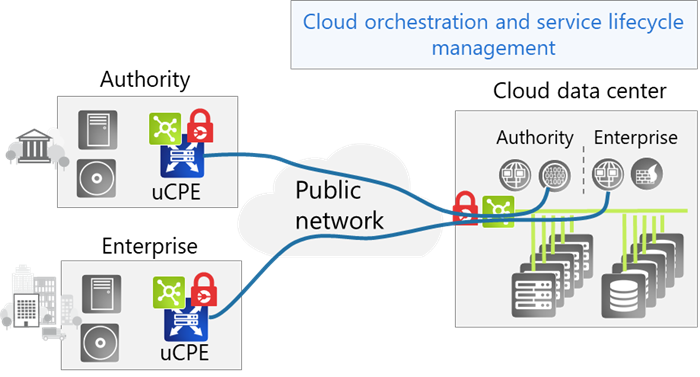
Figure 1: Secure access to the cloud with shared resources in the cloud
Many enterprises are reluctant to host data and applications in public clouds for security reasons. For those customer, air-gapped servers should be installed in separated protection zones and robustly protected at the lower network layer in combination with encrypted connectivity. Businesses can now harness the benefits of operational synergies in the cloud with zero compromise on security.
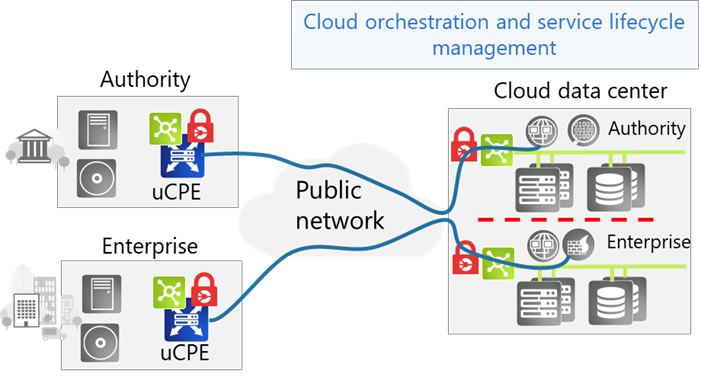
Figure 2: Encrypted access to the cloud with air-gapped, dedicated resources for highest security requirements
If you want to learn more about secure hosting in the cloud, please visit our demo at the ADVA booth during the MPLS + SDN + NFV World Congress in Paris from April 10 to 13. Jointly with IBM, our global systems integration partner, we’re showcasing a typical use case for NFV-based enterprise services and explaining how additional protective controls can meet the needs of customers with high security requirements.
