People already have a difficult time understanding SD-WAN and uCPE. Now Gartner has thrown SASE into the mix. How are these technologies related?
Let’s start with SD-WAN
Software-defined wide-area network (SD-WAN) is an application that is responsible for providing dynamic virtual private networks (VPNs), hybrid WAN routing and network security capabilities to build an overlay VPN between enterprise branches (mesh network) or between enterprise branch sites and corporate data centers (hub-and-spoke network). The initial driver for SD-WAN was providing a lower cost alternative to MPLS-based VPNs. This was achieved by enabling enterprises to use a variety of network access technologies such as LTE, DSL, etc. and ensuring the availability of WAN connectivity across these diverse networks. But SD-WAN can also provide the ability to quickly turn up new sites, manage the traffic to each site, and co-exist with MPLS VPNs.
There are a variety of SD-WAN suppliers and solutions in the market today, and they usually include the following functions.
A set of access nodes at the user sites that include many or most of the following:
- A routing and tunneling engine
- Hybrid WAN, including the ability to send traffic to more than one uplink
- Firewall and security functions
- QoS and access policy enforcement including application-level monitoring and steering
- Network loss and latency measurement
- WAN optimization, including one or more of caching, compression, forward error correction, prioritization, and load balancing
A central controller for:
- Administering the network topology
- Setting and distributing policies for QoS and access
- Reporting usage and performance
Note that the access nodes can be implemented at the end user site as an appliance, a software application running bare metal on a server, or as a virtual network function (VNF) running on a uCPE (more on that below).
The SD-WAN application be self-managed by the enterprise or accessed as a managed service.
But SD-WAN is the application, not the delivery mode or instantiation.
On to uCPE!
Universal customer premise equipment (uCPE) is an application of network functions virtualization (NFV) technology. uCPE provides an open, multi-vendor edge cloud platform on which a multitude of service provider managed and private customer workloads – including SD-WAN, networking and security applications – can be deployed and managed.
We can further refine the definition of uCPE by looking at some of the main characteristics of the solution:
- Software applications – provide the ability to control the features and capabilities of the uCPE device via software configuration rather than swapping out proprietary hardware devices
- Running on an open software platform – this could be our ADVA Ensemble Connector or a standard distribution of Linux
- Hosted on an open standard COTS server – not a proprietary device
- Deployed at the customer site – as opposed to a next-gen central office or data center
- Centrally-managed with rich operational tools - that can automatically turn up and manage multi-vendor, multi-cloud deployments via a common set of edge cloud management tools
Initially the software applications mentioned above were delivered as VNFs. Cloud-native enabling technology continues to mature, and many of these functions will migrate to container network functions (CNFs). As the name implies, the initial VNF workloads were focused on networking and communications applications such as routers, firewalls, SD-WAN and WAN optimization. But uCPE can host any type of workload including IoT, LTE, 5G, or user-defined applications.
An ideal uCPE platform should also include a rich set of embedded networking and management capabilities. For example, our Ensemble Connector software provides the base networking capabilities to deploy and manage the physical infrastructure and various access underlay network technologies.
Once we deploy and establish management connectivity to the uCPE platform, SD-WAN and other applications are plugged into the WAN interfaces where they manage the overlay applications.
One of the benefits here is that the Connector uCPE OS is independent from the SD-WAN application. If there’s a problem with the SD-WAN application, you can still remotely access, manage and recover the uCPE device without sending a technician to site.
Additionally, some SD-WAN applications do not natively support all the various types of local networks that may be attached to the uCPE device. Wireless/LTE is one of the primary culprits. Connector provides an agnostic hosting platform that can manage different physical interfaces and access network types. It also provides a common presentation of these networks as a suite of generic IP interfaces that SD-WAN VNFs can access.
An ideal uCPE platform should also include a rich set of embedded networking and management capabilities.
The importance of independent layers
Some SD-WAN vendors are positioning their solutions as uCPE platforms that can host VNFs in addition to their SD-WAN functions. But their ability to support multi-vendor VNFs and customer workloads is very limited. In many cases, it requires development work to integrate third-party software. Also, one of our key differentiators is zero-touch provisioning (ZTP) enabling automated deployment, along with management of this multi-vendor (hardware and VNF) solution stack – and this is an area that most SD-WAN vendors have yet to address.
Here’s an example that illustrates what happens when you attempt to use an SD-WAN package to also host VNFs:
- The operator selects supplier A for their SD-WAN solution as well as for a uCPE hosting platform.
- The operator pitches an SD-WAN service from supplier A to their enterprise customers. But in some cases, the enterprise already has a relationship with SD-WAN supplier B.
- How does supplier A – as an SD-WAN application – host an SD-WAN application from Supplier B running as a VNF? There will be all sorts of resource contention for WAN ports, packet processing, managing state, etc.
- And just as important, does supplier B want to rely on a competitor to host their application?
In contrast, service providers who leverage a vendor-neutral and open hosting layer gain these benefits:
- A true multi-vendor system with separate suppliers of servers, hosting software, and VNFs
- Separation of hosting from network functions enables dynamic service deployment and eliminates the vendor lock-in seen when VNFs also provide hosting
- De-risking SD-WAN selection. There will continue to be consolidation in the SD-WAN space, with some suppliers going away. Separating the SD-WAN function from the hosting layer provides a recovery path for replacing SD-WAN VNFs due to technical or commercial reasons
- Optimization at each layer. You can add a new server with lower cost or higher performance, while keeping the VNFs unchanged. Likewise, VNFs can be combined in a service chain to deliver innovative features and to meet customer requirements for particular VNF suppliers
- Networking and operational features. An optimized hosting layer goes beyond just providing a home for VNFs. It also enables advanced networking and operational features, such as zero-touch provisioning, advanced networking, fault and alarm management, and security.
- Support for a wide range of COTS servers. A dedicated hosting layer will support a much broader range of hardware platforms and features than will an SD-WAN VNF that also provides hosting.
What about SASE?
Now we have a clear and perfect understanding of SD-WAN and uCPE (I hope 😊). What about SASE?
Gartner defined SASE (pronounced “sassy”) as secure access service edge. SASE is intended to address the accelerating trend of a highly mobile, decentralized workforce that accesses applications outside of the corporate data center. Enterprises secure their IT network at this entry point, creating an intranet versus the external network. The intranet is considered to be a secured and trusted zone. Different sites are connected through a WAN, with SD-WAN being a more sophisticated approach.
Any remote user accesses a VPN to gain access to the trusted enterprise intranet. Such a security architecture does not meet the requirements of an increasingly mobile workforce and cloud-hosted appliances. It’s inefficient for these workers to be on a corporate VPN to access software-as-a-service (SaaS) applications. Doing so forces all their traffic to be routed into a corporate data center for inspection.
In contrast, SASE combines network security functions (such as SWG, CASB, FWaaS and ZTNA), with WAN capabilities (i.e., SD-WAN). SASE aims to reduce cost and complexity by moving security policy decisions closer to the user, device, or service. SASE will provide centralized policy control based on the identity and location of the user or device, the time of day, the risk/trust assessment of the device, and the sensitivity of the application/data being accessed.
Gartner’s definition of SASE implies a high level of flexibility and dynamism. Their solution architecture requires most of the security features and policy decision-making to happen in a cloud-based platform. These capabilities can be applied everywhere and anywhere via a global network of interconnected points of presence (PoPs). A typical customer site deployment will only require a thin client as a tunnel endpoint. The client handles limited traffic processing before encrypting the data and forwarding it to the SASE PoP.
Infoblox provided a good summary of the characteristics of SASE:
- Cloud-native architectures with containerized micro-services – use of cloud-native design principles and containerization for superior agility, flexibility, speed, and scalability
- Integrated network and security services – simplified management of diverse WAN networking and security services available through a common platform
- Cloud-managed on-demand services – combining the cloud with consumption-based usage in delivering elastically scalable networking and security services to globally distributed, edge-centric enterprises
- Centralized policy control – a unified framework for deploying and enforcing security policies to all devices and endpoints across the network
- Local survivability – maintaining local access to essential network services such as DNS at the branch level should a disruption in WAN connectivity to headquarters occur
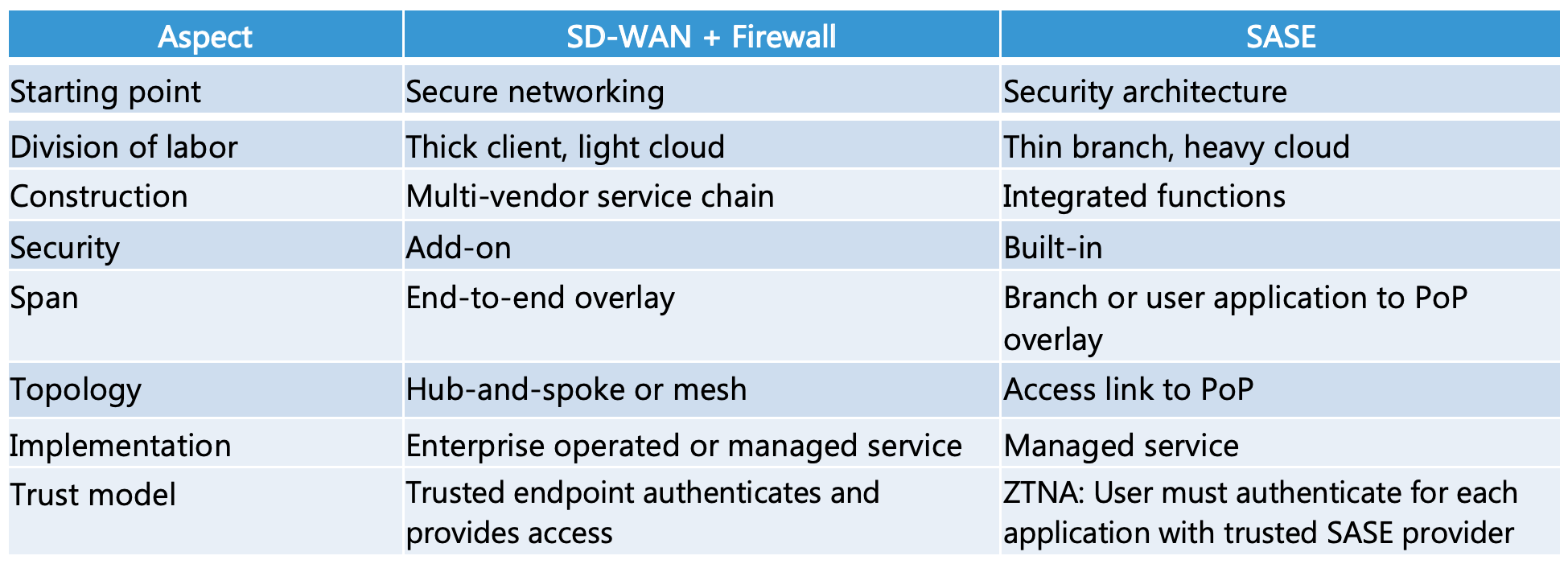
Here’s my comparison of SD-WAN plus firewall versus SASE: